Kamailio with TLS module
The “tls” module is specifically designed to add TLS (Transport Layer Security) support at the TCP transport level, and allows to manage traffic that uses SIPS (SIP Secure) for SIP encryption. All details are available on the official Kamailio documentation for the [tls] module (https://kamailio.org/docs/modules/stable/modules/tls.html). Here we will see how to activate it on our Kamailio installation.
What we need
To configure Kamailio with TLS support we have to install the specific module (e.g. kamailio-tls-5.5.3 - package versions are available here). Then we need a certificate with its private key, which is validated by a Certificate Authority. For internal testing purposes we could use a self-signed certificate, but this will not be valid in case of interconnections with real systems, such as official VoIP providers for example. At this point we are able to accept SIP traffic encrypted over TLS, but to have a very secure communication we should also validate the certificate of the remote client/server with which kamailio exchanges messages, and to do this we need the CA certificate of the remote element.
Kamailio TLS configuration
After installing the kamailio-tls package we must obtain a certificate for our server with the CA of the remote client/server, then we can proceed with the system configuration.
In the file /etc/kamailio/tls.cfg we configure the parameters relating to the exchange of certificates, while in the configuration file kamailio.cfg we activate TLS support.
tls.cfg configuration file
The tls.cfg file contains the parameters for exchanging certificates, both when Kamailio is a server in the data flow and when it is a client.
Kamailio server role [server:default]:
- method: sets the TLS protocol method (es. TLSv1.2+)
- verify_certificate: yes/no if enabled it will force certificate verification when connecting to other SIP servers
- require_certificate: yes/no when enabled Kamailio will require a certificate from a client connecting to the TLS port
- private_key: sets the private key file name(PEM)
- certificate: sets the certificate file name (PEM)
- ca_list: sets the CA list file name, this file contains a list of all the trusted CAs certificates used when connecting to other SIP implementations
Kamailio client role [client:default]:
- verify_certificate: yes/no if enabled it will force certificate verification when connecting to other SIP servers
- require_certificate: yes/no when enabled Kamailio will require a certificate from a client connecting to the TLS port
- ca_list: sets the CA list file name, this file contains a list of all the trusted CAs certificates used when connecting to other SIP implementations
kamailio.cfg configuration file
Once we have configured the parameters for the exchange of certificates, we can activate the use of TLS in the main Kamailio configuration file.
First of all, let’s enable the global define #!define WITH_TLS at the beginning of the file, and then make sure that the TLS specific configuration sections are present.
#!ifdef WITH_TLS
enable_tls=yes
## Listen on TLS Port
listen=tls:PRIVATE_IP4_ADDR:SIPS_PORT
/* upper limit for TLS connections */
tls_max_connections=2048
#!endif
#!ifdef WITH_TLS
loadmodule "tls.so"
#!endif
#!ifdef WITH_TLS
# ----- tls params -----
modparam("tls", "config", "/etc/kamailio/tls.cfg")
#!endif
TLS at work
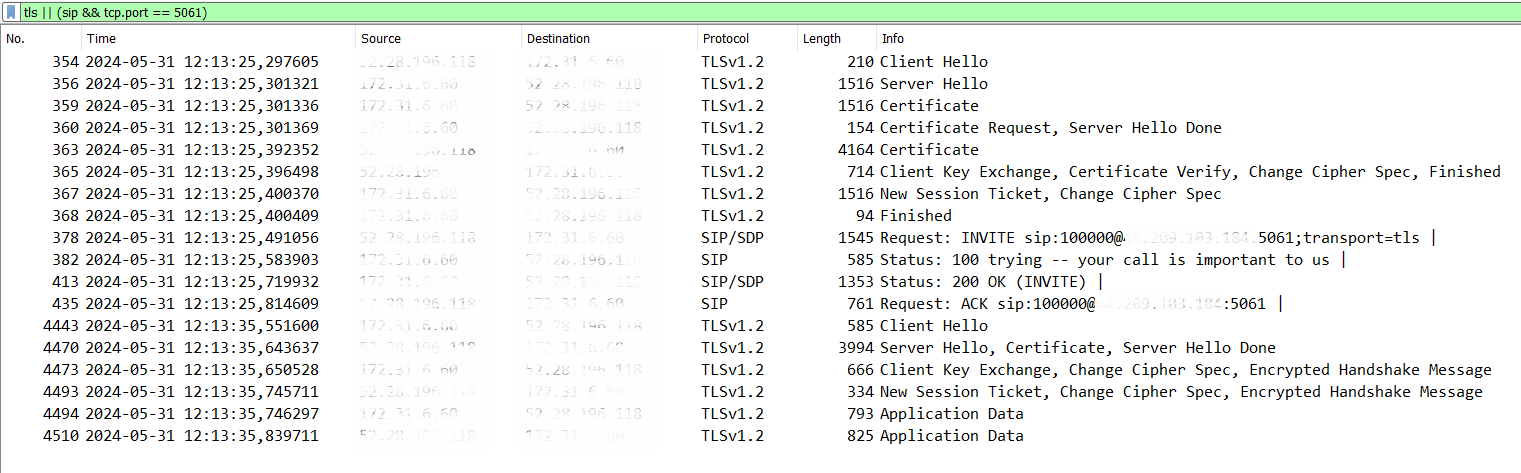
Once the configuration is complete and Kamailio is restarted, we can manage the first call over TLS, and with tcpdump active on the server we can also see in detail the TLS handshake phase.
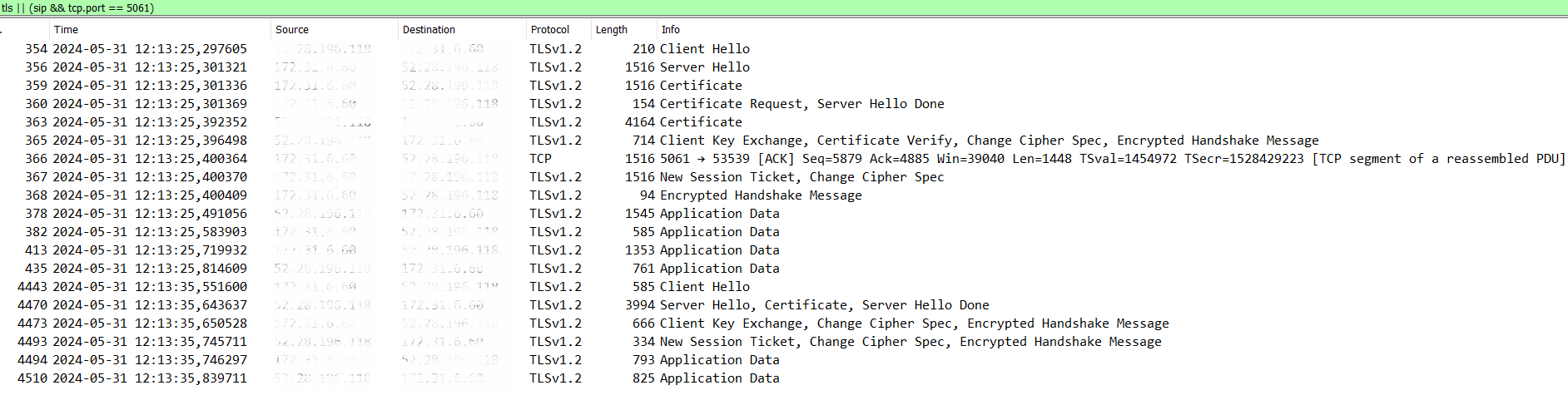
In this case, Kamailio is the destination server that receives the Client Hello message and initiates the TLS handshake by sending the client its certificate and at the same time requesting the client to transmit its own certificate in order to validate it. This is because we have configured Kamailio with verify_certificate = yes and require_certificate = yes parameters. Once the handshake is completed, the encrypted data exchange begins. Here we have the private key used to for the encryption, so we can also decode the real SIP traffic.